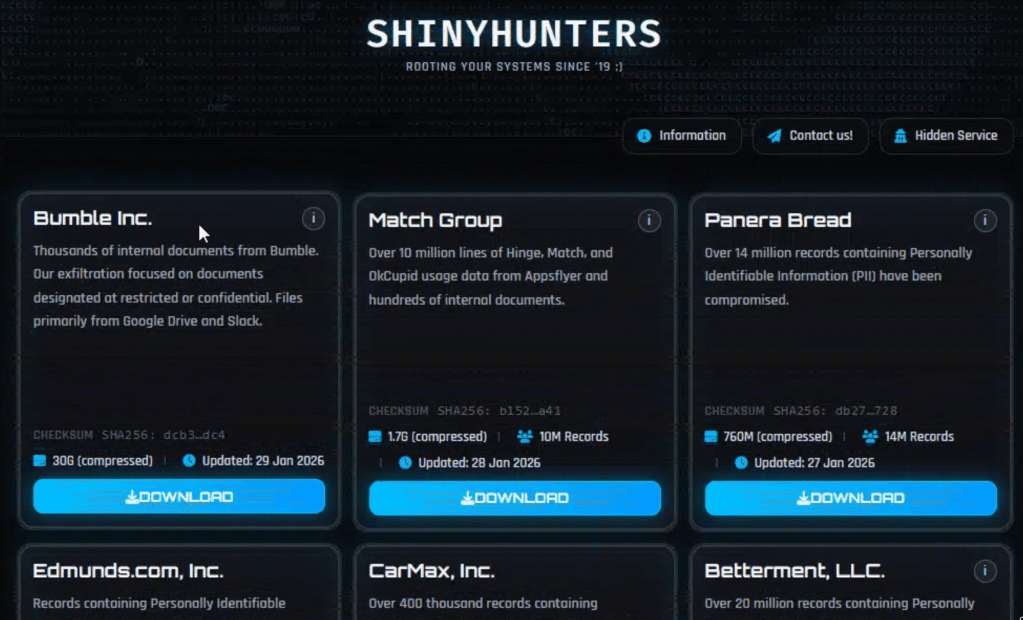
Notorious extortion group ShinyHunters released tens of GB of files it claims to have stolen from dating apps Hinge, Match, OkCupid and Bumble. While there is no official confirmation about how the companies were breached, researchers believe the group’s activities triggered a recent Okta advisory about a rise in voice-based social engineering attacks supported by automated phishing kits.
The latest data leak that impacts dating services and apps come after the group had recently posted files stolen from SoundCloud, CrunchBase, Betterment, CarMax, Edmuns.com, and Panera Bread, suggesting the list of victims could be or grow larger.
CSO
In operation since 2020, ShinyHunters, also tracked as UNC6040, has stolen data from many well-known brands and organizations over the years. The group’s known techniques involve impersonating IT staff to compromise employee accounts.
Last September, security companies reported that ShinyHunters joined forces with two other notorious hacker groups, LAPSUS$ and Scattered Spider. The data dumps over the past week are likely the result of a much larger hacking spree the new collective has been engaged in recently.
Security firm Silent Push detected new phishing infrastructure that matches the tactics, techniques, and procedures (TTPs) of SLSH (Scattered LAPSUS$ Hunters) being set up to target more than 100 high-value organizations in the past month. The infrastructure involves a “Live Phishing Panel” that allows attackers to perform a man-in-the-middle attack on login sessions in real-time with the goal of capturing credentials and multi-factor authentication (MFA) tokens for single sign-on (SSO) platforms, including Okta.
“We are aware of claims being made online related to a recently identified security incident,” a Match Group spokesperson told CSO. “Match Group takes the safety and security of our users seriously and acted quickly to terminate the unauthorized access.”
“We continue to investigate with the assistance of external cybersecurity experts,” the company said. “There is no indication that user log-in credentials, financial information, or private communications were accessed. We believe the incident affects a limited amount of user data, and we are already in the process of notifying individuals, as appropriate.”
Bumble and Panera Bread did not respond to requests for comment.
Phishing kits designed for voice attacks
Okta warned last week about an increase in attacks against Okta, Microsoft, and Google accounts that are enabled by commercial phishing kits specifically designed to make voice-based social engineering attacks more effective.
Phishing kits are collections of automated tools, scripts, and website templates that allow cybercriminals to create fake websites and launch credential-stealing attacks. However, when victims use MFA, the success of these tools can be quite low because the attackers can’t guess what type of MFA an account has enabled. Is it a code generated by a mobile app? Is it a code sent via SMS? Is it a push notification sent to their mobile device that they must tap on? Websites can offer multiple MFA options and it’s up to users and companies to configure them.
But when combined with voice calling, also known as voice phishing or vishing, these attacks become much more powerful, because the attacker can test the user’s credentials in real-time on the legitimate site, see what MFA type they get prompted for, and modify their phishing page in real-time.
“This real-time session orchestration provides a new level of control and visibility to the social engineer,” Okta researchers said. “If presented a push notification (type of MFA challenge), for example, an attacker can verbally tell the user to expect a push notification, and select an option from their C2 panel that directs their target’s browser to a new page that displays a message implying that that a push message has been sent, lending plausibility to what would ordinarily be a suspicious request for the user to accept a challenge the user didn’t initiate.”
These hybrid attacks can also defeat one of the more powerful MFA techniques designed to counter the automated phishing of MFA codes: push notifications that ask users to input into their mobile authenticator app a number generated by the legitimate website, instead of inputting on the website a number generated by the app.
This fails with automated attacks because if the user sees a phishing page instead of the legitimate website, they don’t know what number to enter inside their authenticator app. But an attacker on the phone with them can tell them — or can modify the phishing site on-the-fly to display the number they know the legitimate website expects.
Alon Gal, CTO of cybercrime intelligence firm Hudson Rock, told CSO that the vishing techniques described by Okta in its advisory align with ShinyHunters’ known TTPs: impersonating IT support, real-time MFA bypass via phishing kits, credential/session token theft, SaaS data exfiltration.
Gal also noted that he checked the newly leaked data and it matches the named victim companies, which is consistent with previous ShinyHunters claims and releases.
Mitigation
The Okta report has links to previous advisories that include both indicators of compromise and TTPs for known actors targeting SSO logins. Meanwhile, Silent Push advises organizations to inform employees about the ongoing ShinyHunters attacks so they are on alert in case they do get contacted by callers.
Companies should ask employees to verify IT support calls through an official out-of-band channel and should audit their operations support system (OSS) provider logs regularly for events indicating new devices being enrolled to accounts followed by logins from new IP addresses.