As data sovereignty laws fracture the global internet, CSOs are scrutinizing ambitious new compliance blueprints, with their success or failure set to redefine security architectures for a generation.
“Project Texas” may just be the most visible attempt to realign a global platform’s data, access and governance with U.S. jurisdiction and oversight. In practice, it is an in-country operating model: sensitive U.S. user data is localized, access is brokered under U.S. law and an external operator provides independent infrastructure and controls. The name nods to Texas and the U.S. infrastructure anchor; the stakes are global.
I have sat in rooms where a press release swore data was safe behind a new “sovereign” wall, then an auditor asked a simpler question: “Can you show me, right now, where the data is, who touched it and under what authority?” In that moment, architecture becomes language and evidence becomes reputation. This isn’t about slogans. It is about designing systems that leave fingerprints: every access mediated, every key anchored, every event written in ink that cannot be erased.
Headlines tout data sovereignty pledges like Project Texas, but security leaders win by turning them into auditable evidence. A Kearney study found that 78% of executives say they struggle to interpret sovereignty rules consistently across markets. The mandate is shifting from making promises to providing proof — verifiable controls for zero-trust access, in-region keys, immutable logs and continuous validation that regulators and customers can trust.
“Verification regimes work best when they serve everyone’s interests. The reporting company wants a process that does not impose too many burdens or interrupt workflow while allowing it to demonstrate compliance. Oversight bodies want hard data that is difficult to fake and indicates adherence to the regime. Finally, these systems need to be simple enough to be sustained over time.” — J. Michael Daniel, President & CEO, Cyber Threat Alliance and former Special Assistant to President Obama and Cybersecurity Coordinator on the National Security Council Staff
The gap between policy and proof
Big platforms pledge regional data segregation. That’s good for comms. But in the SOC and audit room, what matters is demonstrable proof. A 2025 Nutanix report found that over 80% of IT leaders cite data sovereignty as a primary driver for new cloud architecture decisions — exactly what Project Texas embodies. Can you show that sensitive data stayed in-region, was accessed for a valid purpose, with the right keys?
Closing this gap requires five concrete, testable data sovereignty controls.
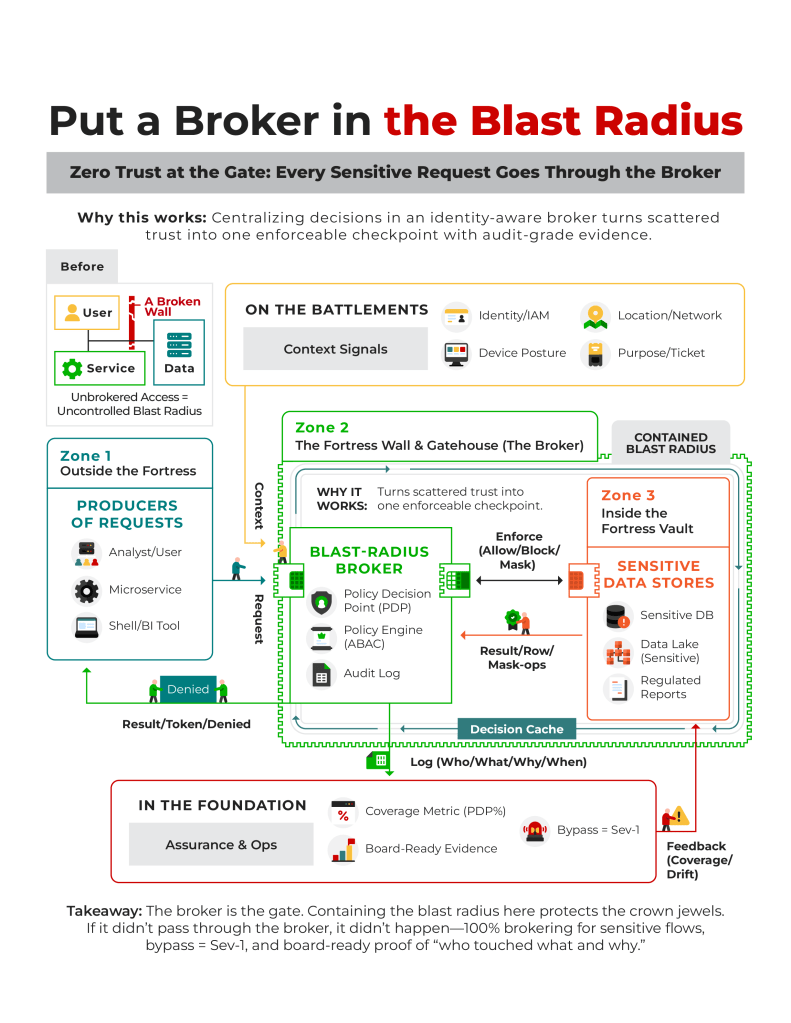
1. Put a broker in the blast radius (zero-trust data gating)
For verifiable control, implement zero-trust data gating by brokering all sensitive data access through a policy decision point (PDP), an identity-aware proxy/API gateway using ABAC (who, what, where, why). This gateway strictly enforces attribute-based rules, banning all direct access to contain the blast radius of any potential breach.
Build this control using your cloud provider’s core services:
OCI API Gateway + OCI IAM + Logging/Audit (or equivalents such as AWS API Gateway/ALB + IAM + CloudTrail/CloudWatch, Azure API Management + Entra ID + Monitor/Activity Log, GCP API Gateway/Apigee + Cloud IAM + Cloud Audit Logs)Treat 100% PDP coverage for sensitive flows as the benchmark. This proves you have eliminated backdoors, collapsing insider risk and lateral movement by ensuring no compromised account can move freely. Ultimately, it provides the board with a single, auditable source of truth for all data access.
“Sovereignty isn’t just a region on a map — it’s an operating model. The hard part isn’t promises, it’s proving every week that keys stay in-country, access is brokered and there are no side paths.” — Ian Rogers, Co-Founder and Data Sovereignty Expert, TEAM Cloud
Michelle Buckner
2. Cryptographically enforce location (in-region keys)
Enforce location by anchoring encryption to in-region keys, making jurisdiction a property of the cryptographic root. This means generating and storing all cryptographic keys within hardware security modules (HSMs) located inside the required jurisdiction, under dual control and geo-fencing every key operation, instead of soft keys in app code, global KMS with single-admin control or cross-border decrypt/unwrap by default.
The critical signal of success is achieving “keys in-region = 100%,” backed by attested logs from the HSM. This provides a mathematical backstop, ensuring that events like undersea cable cuts, foreign cloud breaches or extraterritorial legal demands become non-events for your protected data.
3. Guarantee immutable audit trails
By establishing immutable audit trails, you practically guarantee the integrity of your evidence. This is achieved by streaming all critical logs — from your access gateways, key management systems and data platforms — into append-only, write-once-read-many (WORM) storage that cannot be altered.
The essential metric is achieving lineage coverage greater than 95%, ensuring this timeline is queryable in minutes, not days. This creates an incontrovertible record, giving you the definitive ability to answer any auditor’s question about who accessed what data, from where and under what authority, in near real time.
4. Continuously validate for control drift
Prevent control drift with continuous validation. Proactively test sovereignty safeguards with scheduled red team exercises that simulate cross-border exfiltration and run automated canaries that alert on any policy breach; for example, a decryption attempt from a blocked region. Embed policy-as-code in the CI/CD pipeline so any change that creates an unbrokered data path fails before it ships. Track a simple health metric: canary violations at zero over a rolling 30 days. Most sovereignty programs do not fail on design; they fail when operational rigor erodes.
5. Enable third-party attestation
The final pillar, third-party attestation, transforms internal proofs into externally verifiable evidence. This involves providing regulators and customers with independent assurance without exposing intellectual property. It is achieved through machine-readable policy feeds, read-only portals for log and lineage data and cryptographic proofs from your in-region HSMs. The ultimate validation comes from allowing auditors to witness live red/blue team drills.
This approach fundamentally flips the model from a trust-us narrative to a repeatable, technical verification that anyone can test for themselves.
The 90-day data sovereignty blueprint
- Day 0: Inventory sensitive data, enable WORM logging, choose a PDP pattern
- Day 30: Front sensitive stores with the PDP, localize keys, publish initial PDP coverage and keys in-region metrics
- Day 60: Wire policy-as-code into CI/CD, deploy canaries, build v1 of the attestation bundle for a mock audit
- Day 90: Operationalize continuous validation
The future: AI and automated verification
“Sovereignty you can’t prove is just a promise. The next step is turning intent into verification — and then making verification automatic: In the near-term, AI agents will pre-check controls before deployment and auto-assemble attestation evidence and answer audit questions in plain language with hash-stamped, reproducible proofs.” — Craig McLellan, Founder & CEO, ThinkOn; Data Sovereignty Architect
Emerging strategies will make proof cheaper and stronger.
- AI control validators: Before a release goes live, smart checks compare the rules you say you enforce with what’s actually in your infrastructure-as-code and data catalogs. If they find an unapproved data path, the CI/CD pipeline blocks the deploy.
- Autonomous evidence bundling: Background agents regularly collect the right logs — policy-engine decisions, KMS/HSM key activity and data lineage — and create a hash-stamped, audit-ready package. If anything drifts, they raise a high-priority alert.
- Natural-language audits: You can ask, “Show all access to Alpha-US data last week,” and get a reproducible report of who accessed what, when and why, with tamper-evident exports.
- Privacy-preserving compute: Sensitive jobs are run in confidential computing with hardware attestation and can produce zero-knowledge proofs that data was processed “in region with key X” without exposing the data or the code.
- Attestable vendors and verifiable routes: Suppliers publish machine-readable proof of their controls that you can ingest into a trust dashboard and the network provides signed path records to show traffic stayed in-country.
The CSO bottom line
Cybersecurity leadership across IAM, supply chain and AI shows a consistent pattern: simple, measurable controls prevent complex crises. Data sovereignty is no different. A 2025 Pure Storage survey reported that 92% of global executives now view data sovereignty as a top-tier business risk.
If you can’t measure it, you can’t promise it. If you can’t prove it, you didn’t do it.
Engineer for verifiability by design. Replace press releases with evidence: brokered access, in-region keys, immutable logs and continuous validation. This is how security leaders turn public commitments into durable trust.
This article is published as part of the Foundry Expert Contributor Network.
Want to join?